Ports
SUSE Manager Server
Some ports are only relevant if you actually run the related service on the SUSE Manager server.
- 67
-
Inbound / TCP/UDP / DHCP
Required when SUSE Manager is configured as a DHCP server for systems requesting IP addresses.
- 69
-
Inbound / TCP/UDP / TFTP
Used when SUSE Manager is configured as a PXE server and allows installation and re-installation of PXE-boot enabled systems.
- 80
-
Inbound / TCP / HTTP
Client and proxy server requests travel via HTTP or HTTPS.
- 80
-
Outbound / TCP / HTTP
Used to contact SUSE Customer Center/Novell Customer Center.
- 443
-
Inbound / TCP / HTTPS
All Web UI, client, and proxy server requests travel via HTTP or HTTPS.
- 443
-
Outbound / TCP / HTTPS
SUSE Manager uses this port to reach SUSE Customer Center (unless running in a disconnected mode with RMT or SMT-as described in [disconnect-setup]).
- 5222
-
Inbound / TCP / osad
When you wish to push actions to clients this port is required by the
osaddaemon running on your client systems. - 5269
-
Inbound/Outbound / TCP / jabberd
Needed if you push actions to or via a SUSE Manager Proxy.
- 4505
-
Inbound / TCP / salt
Required by the Salt-master to accept communication requests via TCP from clients. The connection is initiated by the client and remains open to allow the master to send commands. This port uses a publish/subscribe topology; the client subscribes to notifications from the master.
- 4506
-
Inbound / TCP / salt
Required by the Salt-master to accept communication requests via TCP from clients. The connection is initiated by the client and is open only when needed. Usually, clients will open this port when they have to report results to the master, such as when a command received on port 4505 has finished. This port uses a request/response topology; the client sends requests to the master.
- 25151
-
TCP
For cobbler.
- 8050
-
Inbound / TCP / websockify
Needed to access graphical console of virtual machines from SUSE Manager web interface.
- 2828
-
Internal /
Satellite-search API, used by the RHN application in Tomcat and Taskomatic.
- 2829
-
Internal /
Taskomatic API, used by the RHN application in Tomcat.
- 6868
-
Internal
Auditlog-keeper to database.
- 6888
-
Internal
Auditlog-keeper API, used by the RHN application in Tomcat.
- 8005
-
Internal
Tomcat shutdown port.
- 8009
-
Internal
Tomcat to Apache HTTPD (AJP).
- 8080
-
Internal
Tomcat to Apache HTTPD (HTTP).
- 9080
-
Internal
Salt-API, used by the RHN application in Tomcat and Taskomatic.
- 32000
-
Internal / TCP
Port for a TCP connection to the Java Virtual Machine (JVM) that runs Taskomatic and the search (satellite-search).
|
Ephemeral Ports
Anything from port 32768 on (more exactly, what you can see with |
This image is a graphical representation of the ports used in SUSE Manager:
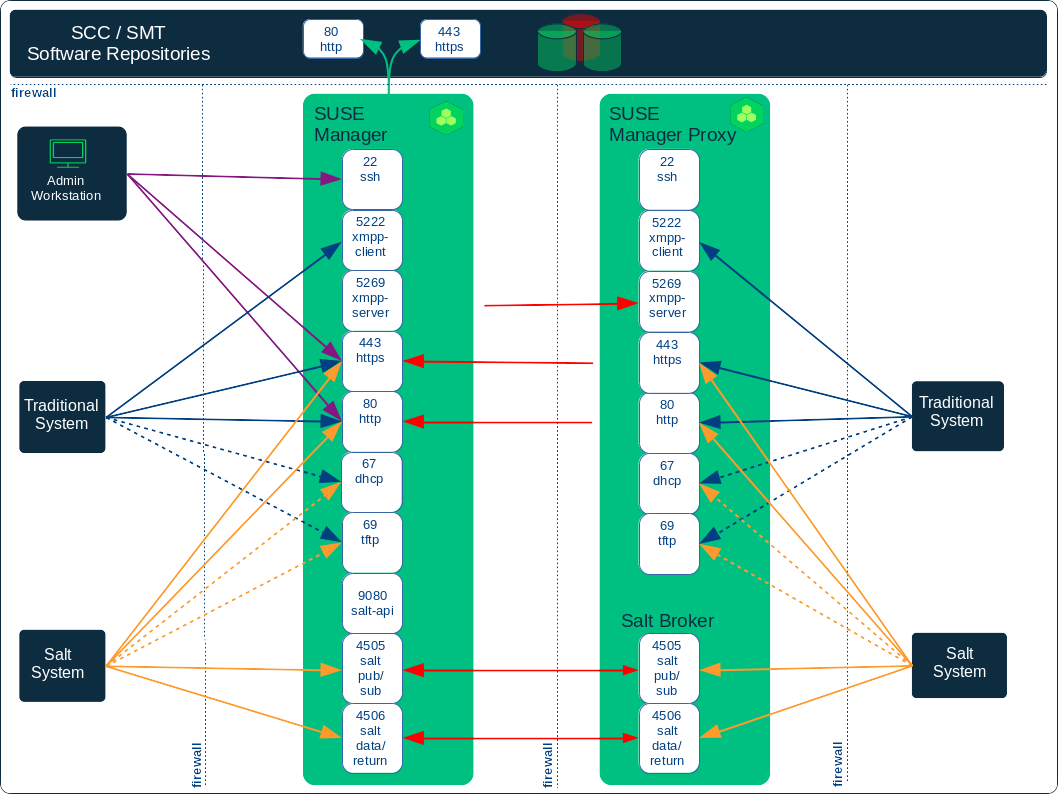
Port 80 (http) is not used to serve the Web UI, and is closed in most installations. Port 80 is used temporarily for some bootstrap repositories and automated installations.
SUSE Manager Proxy Server
- 22
-
Inbound /
Required when using ssh-push or ssh-push-tunnel contact methods. Check-in on clients connected to a SUSE Manager Proxy will be initiated on the SUSE Manager Server and “hop through” through to clients.
- 80
-
Outbound /
Used to reach SUSE Manager.
- 5222
-
Inbound / TCP
For push actions and connections issued by
osadrunning on the client systems. - 5269
-
Inbound/Outbound / TCP
For push actions with the server.
SUSE Manager Client
- 22
-
Inbound / SSH
Required when using ssh-push or ssh-push-tunnel contact methods.
- 80
-
Outbound
To reach the SUSE Manager server or SUSE Manager Proxy server.
- 5222
-
Outbound / TCP
For push actions with the server or proxy server.